Hello Everyone!
This is my first write-up.
I am Lohith Gowda M (Security Engineer). Due to COVID-19, most of the employees got the work-from-home option. It helped me to learn something new in Bug Bounty. I started my bug bounty journey in June 2020.
Working as a Security Engineer and part-time Bug Bounty is a great way to learn something new in this field, and we can also implement it in our daily working life.
I thank my team (Vishva, Harish) and Hacktify Cybersecurity for their support and guidance.
This write-up about the Bigbasket Insecure Data Storage Vulnerability
I found one of the Bigbasket apps using allow backup method=true
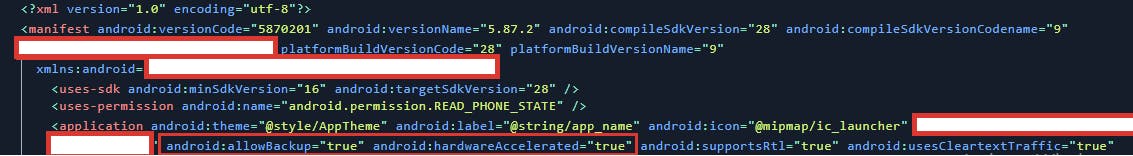
What is allow backup flag in Android?
The android:allowBackup attribute defines whether application data can be backed up and restored by a user who has enabled USB debugging. If the backup flag is set to true, it allows an attacker to take the backup of the application data via ADB even if the device is not rooted. Therefore, applications that handle and store sensitive information such as card details, passwords, etc. should have this setting explicitly set to false because by default it is set to true to prevent such risks.
<application android:allowBackup="false" </application>
ADB Backup feature is a good tool for backing up all of your files. If it’s enabled, malicious users who have your phone can copy all of the sensitive data for this app on your phone. It was found that if an attacker had access to an unlocked phone, they could take any data from the application’s sandbox through ADB’s backup feature.
If android:allowBackup="true" we can easily extract any data from the root storage (Android shared Preferences and Db) if data is not encrypted.
Most of the Bug Bounty program will not accept this bug because of its required physical access to the device. But if you got any sensitive data related to the internal infra, report it immediately.
For this exploitation, I used the Genymotion emulator and Kali Linux for ADB debugging.
Installed Genymotion on my machine (Available for
Windows, Linux, and Mac OS)After that, installed the Android device on my emulator
Android v 8.1The setup was completed, and then I installed one of the Big Basket apps on my device.
I used the following command for debugging the application on Kali Linux.
ADB Connect to the device

Vrified device is connected or not.

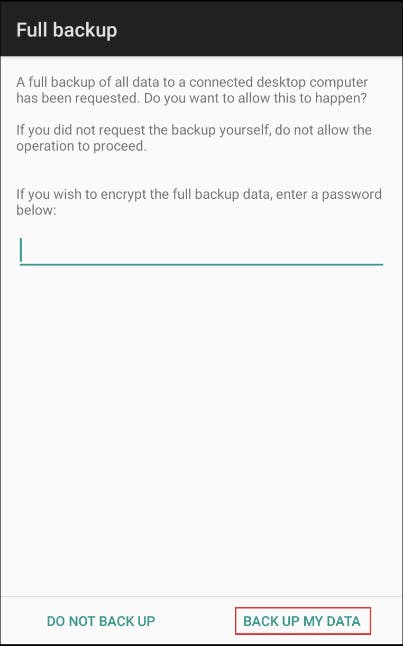
Then I entered the command for backup mobile along with the package name.
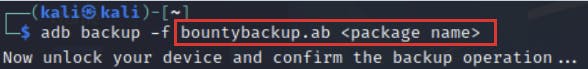
The backup screen on the device. Please click on backup my data.
Once we confirm, it will create an Android backup file with a .ab extension. Usually, the first 24 bytes will be the header. So, we will use the DD tool to remove the first 24 bytes and create a tar file of the remaining part. This can be done as shown below (Use the below command for any backup file). Some other DD commands are available but sometimes it will not work, so I used this one).
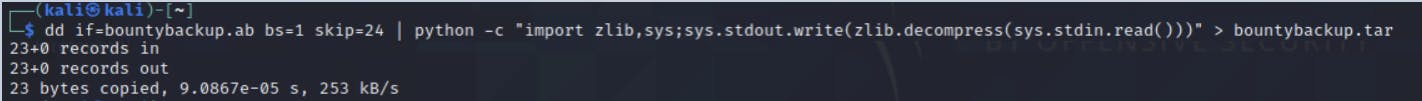
The above command skips the first block from the input file, which is the header part of our Android backup. (This one example file, not the real one, usually will give a large number of records here only 23 bytes)
Now, create a .listfile from the tar file we generated in the previous step. This is to ensure proper order when repacking the backup.
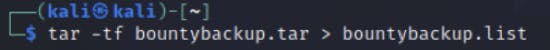
We should have the following files with us now. (You can give any name for a backup file, but the package name should be the same)
bountybackup. ab - Actual Android backup was taken from the device
bountybackup.tar - File generated using dd
bountybackup. list - File generated using the tar file
We can simply extract the bountybackup.tar file using the following command
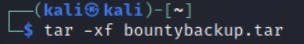
Backup File
Once this backup procedure is completed, then we have a new folder named
apps. We can get into this directory to view the app-specific information.Navigate to the package name folder and go to the SP folder.
What is an SP Folder in Android?
Android Shared Preferences: a common component of Android applications is a set of APIs that manages the developer data of every type, providing a clean way to permanently store and retrieve them from the device. They are used almost in every Android app.
Now We have a SP folder that contains the XML file storing our target app data. I found internal dashboard IP and secret tokens here.
Here is some POC of my Findings
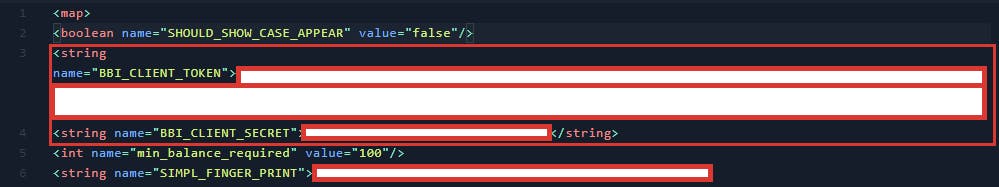
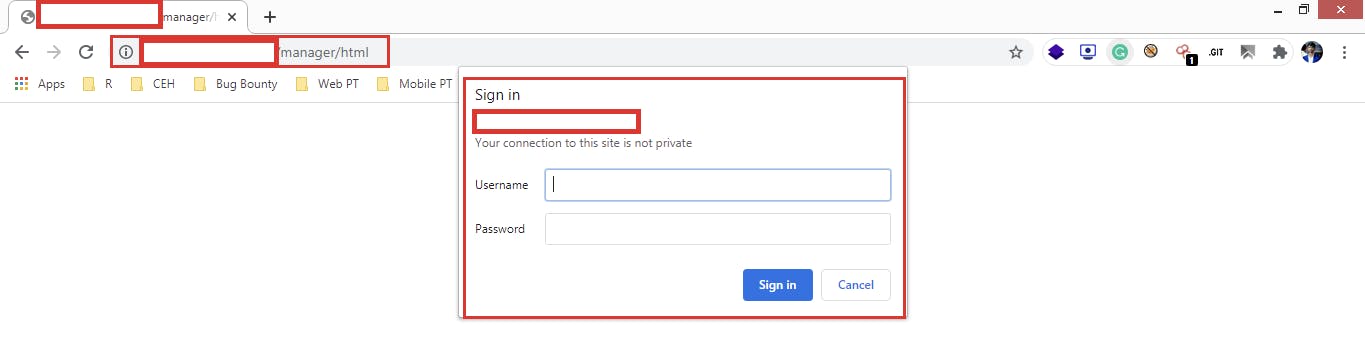
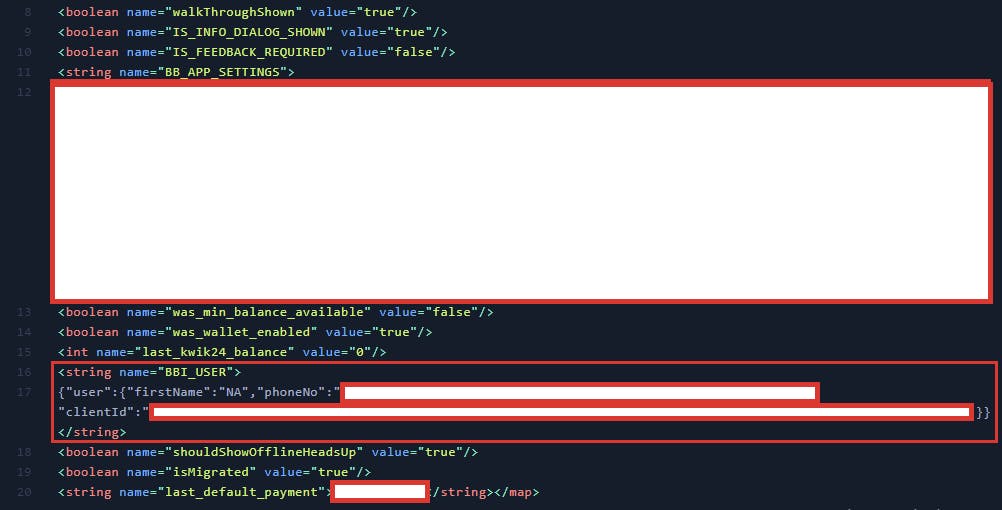
I’ve been rewarded by their Security team and acknowledged in their Hall of Fame.
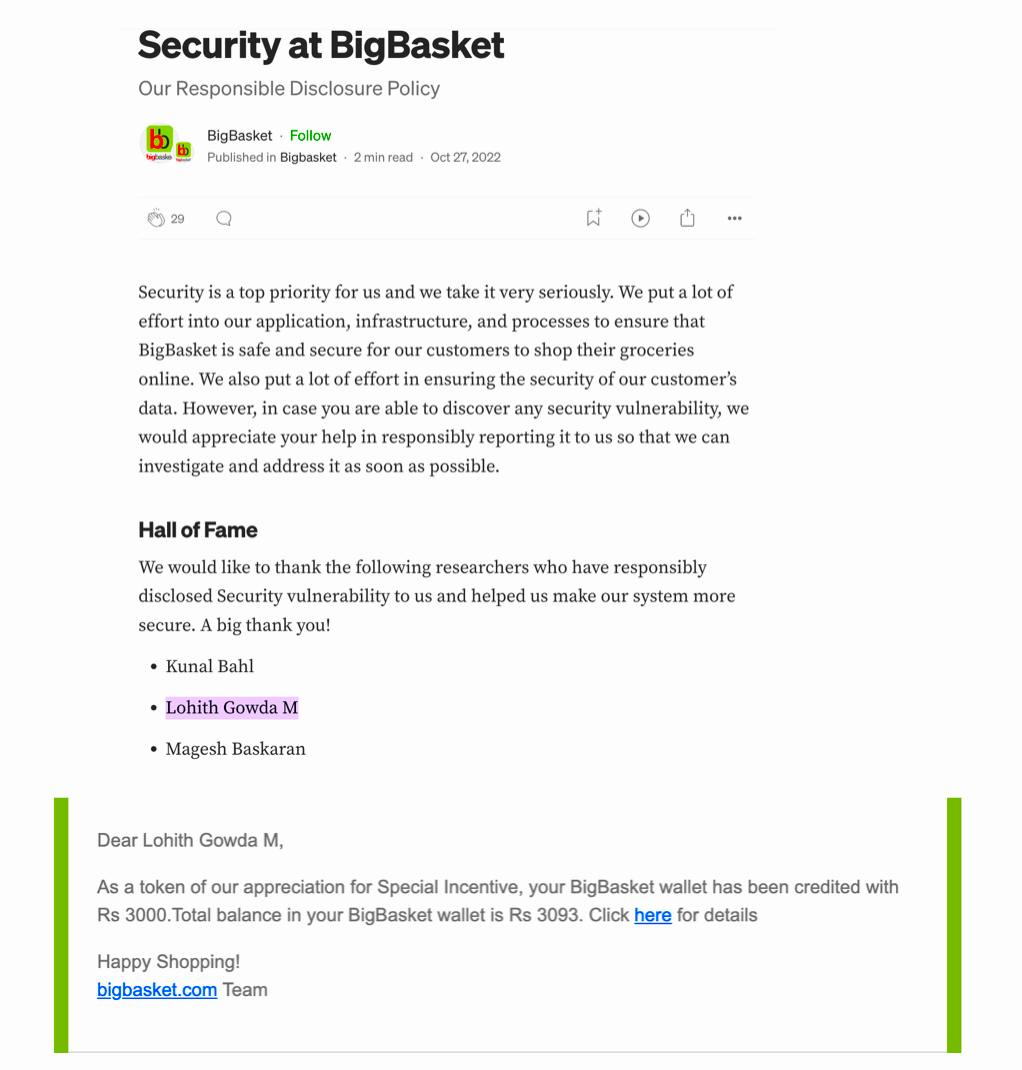
Report Timeline:
Mon, 5 Oct 2020, 01:04 - Bug Reported To Big Basket Security Team.
Tue, 6 Oct 2020, 10:00 - Got First Response from Team
Mon, 12 Oct 2020, 18:25 - Accepted
Tue, 8 Dec 2020, 11:26 - Bug was Marked fixed
Tue, 8 Dec 2020, 07:38 - Re-tested and confirmed the fix
Fri, 8 Jan 2021, 10:27 - Rewarded with Bounty + Hall Of Fame

