Hello People
After a long time, I found one interesting bug in Grofers using a simple Shodan search. The vulnerability could have allowed an attacker to access the internal API monitoring dashboard of Grofers. This is my 2nd report to the Grofers Security team.
What is shodan?
Shodan, a search engine for all ports within the internet, can help enterprises identify and lock down security vulnerabilities Shodan is the search engine for everything on the internet.
Exploit Scenario:
Always my bug bounty journey I will start with shodan search or crt.sh (subdomain enumeration). Recently I found a bug on Dunzo using crt.sh.
Started with simple Shodan dork ssl:grofers
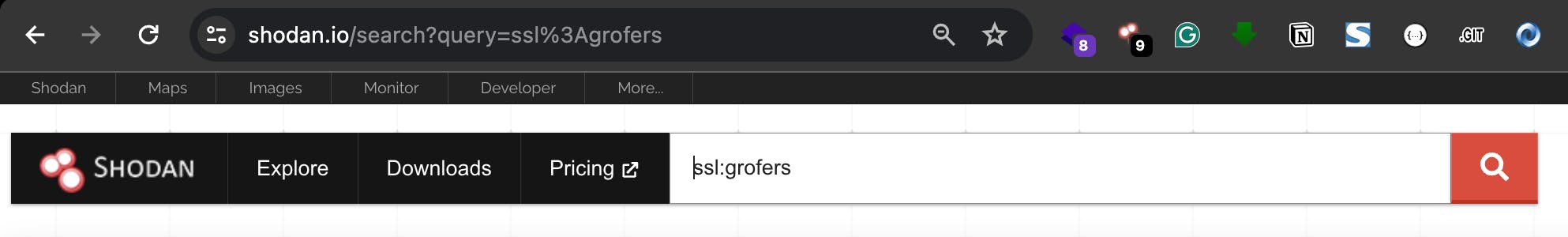
I found multiple hosts related to the Grofers domain. But I observed one interesting host. Immediately opened that host and it’s a Grafana instance login dashboard…
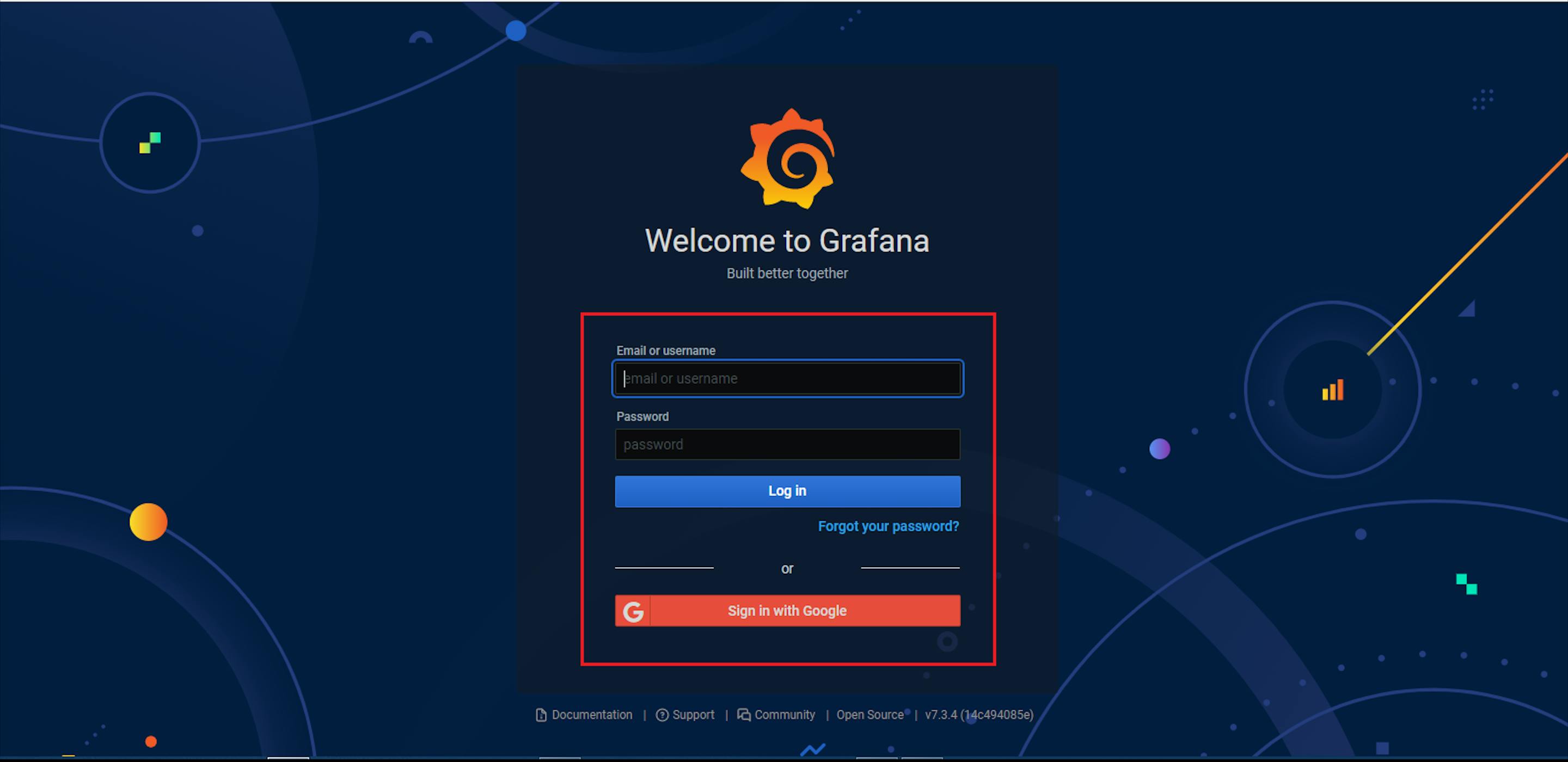
But I don’t know the username and password
Entered default username and password like admin: admin
But the interesting part here is…when I entered the username & password admin: admin, the login page redirected me to the new password page, and got an alert Logged in.
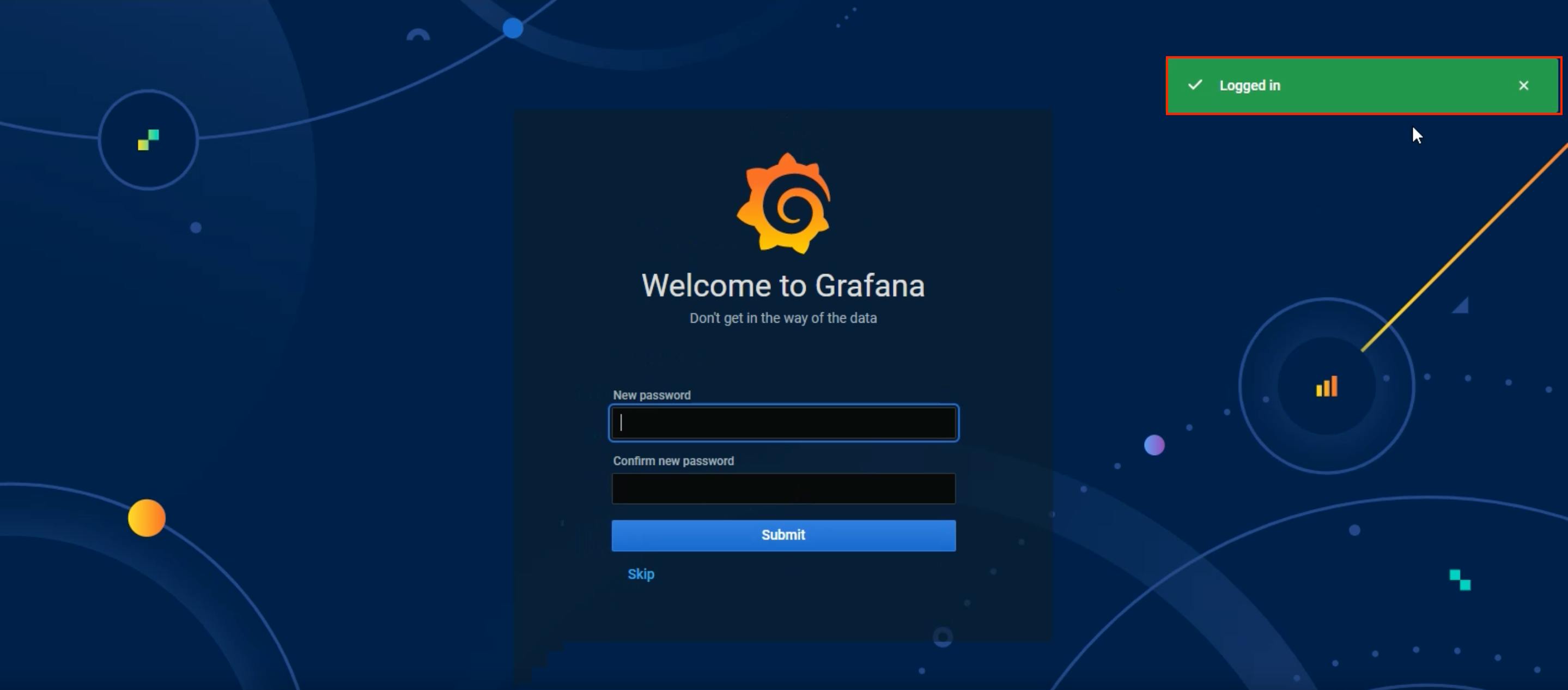
Then again entered the password as admin. At the same time, 2 alerts popped up Invalid or expired reset password code and User password changed
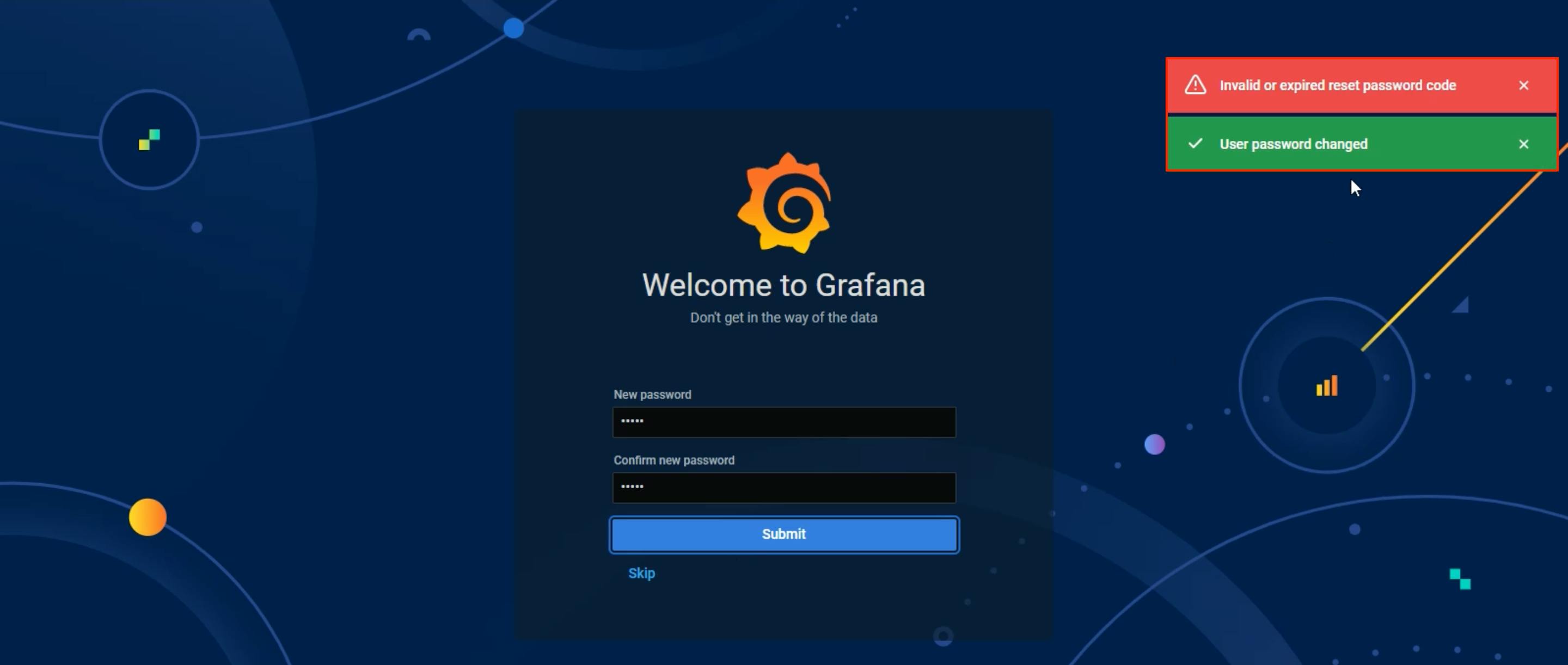
The password got updated. I can access the complete Grafana instance.
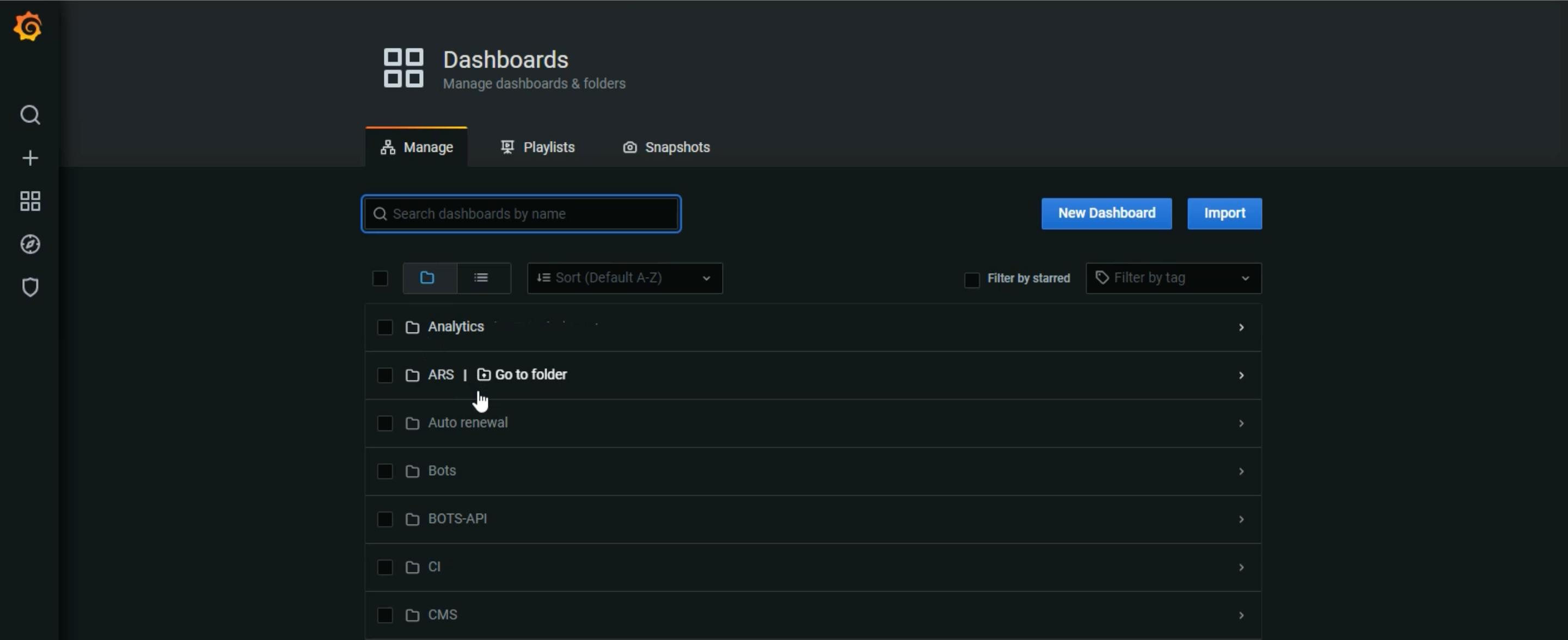
Then I created a report along with POC and submitted it to Grofers security team.
Report Timeline:
08 Dec 2020 - Reported to Grofers Security Team
09 Dec 2020 - First response from the team
15 Dec 2020 - Issue fixed
02 Sep 2021 - Received ₹25kBounty + Hall of fame + Appreciation letter

