Hello Everyone….
I hope you all are doing well. This write-up is about Flipkart's Cross-site scripting Vulnerability.
Cross-site scripting (XSS)
Cross-site scripting (XSS) attacks are a type of injection, in which malicious scripts are injected into otherwise benign and trusted websites. XSS attacks occur when an attacker uses a web application to send malicious code, generally in the form of a browser-side script, to a different end user.
When I was searching for a bug bounty program I came across the Flipkart bug bounty program. In that program for valid submission, Flipkart will mention the bug bounty hunter's name in their Hall of Fame. So I decided to give it a try.
Started hunting on Flipkart
After some recon, I found one issue related to the No Rate limit
Fri, 20 Nov 2020 - Reported that issue to the Flipkart Security team.
Sun, 22 Nov 2020 - Got a response from the team and it’s a Duplicate
Disappointed…
Then I decided that if I give 2nd try
Again started my hunting journey on Flipkart. This time I started with proper recon steps. So started with subdomain enumeration. So I came across one of the Flipkart domain. It’s a normal login form page.
I tried with SQL injection here, but no result. Then tried with a normal XSS payload on a URL parameter. It works. XSS alert popped up.
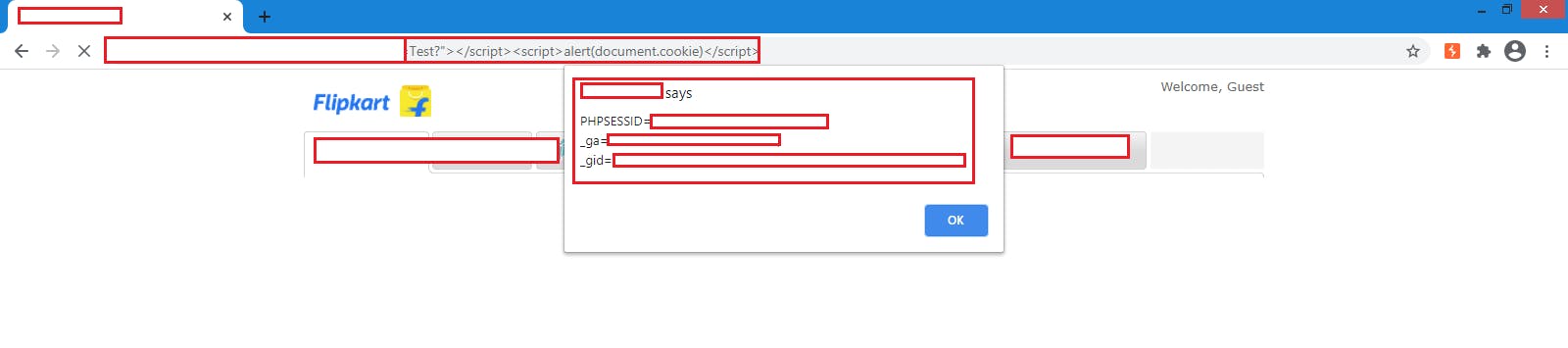
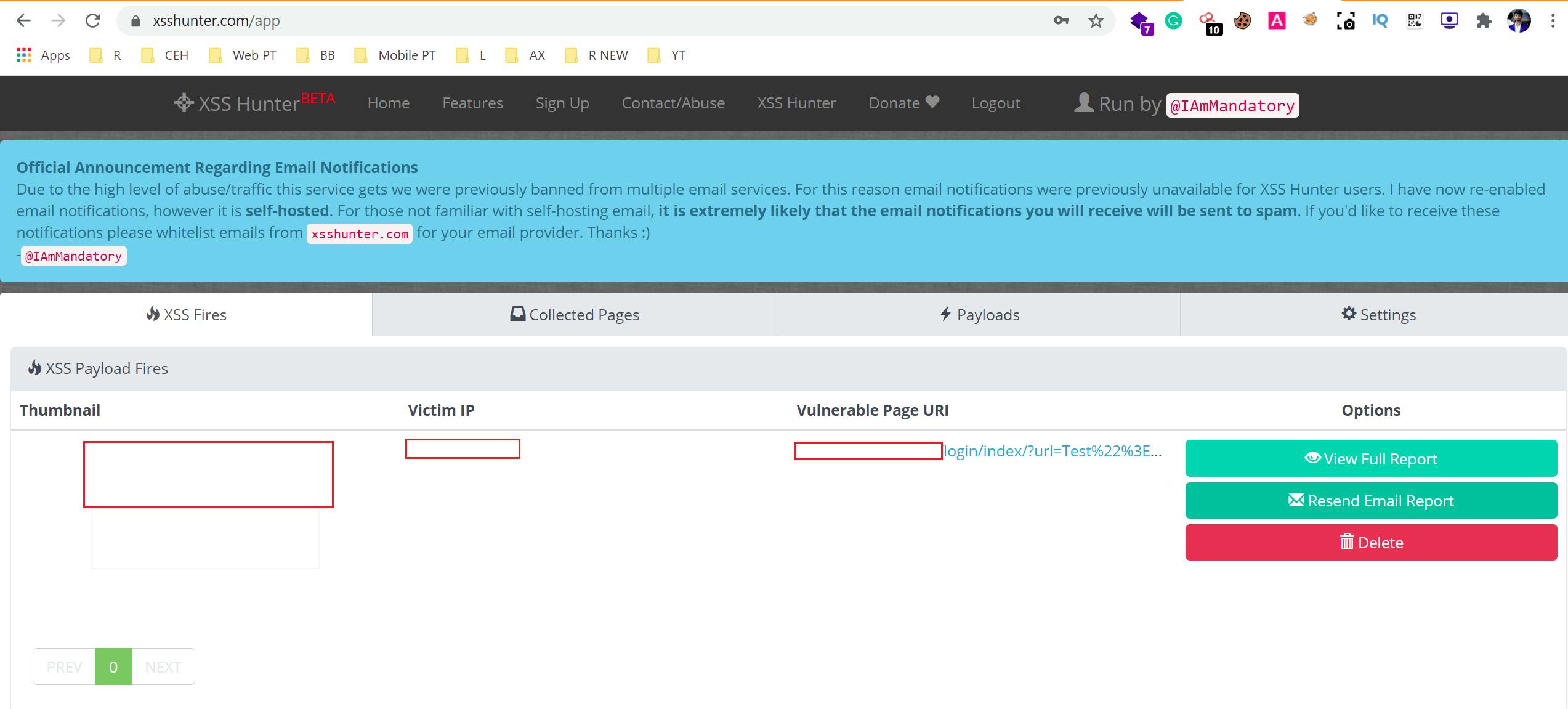
Then I used XSS hunter payload on the same URL parameter.
I received an email from XSS Hunter and POC was created. Here we can be able to see the triggered IP, URL location, and a screenshot of that page.
So finally, I am done with Bug Hunting. So it’s reporting time. Then I prepared a clean report and submitted it to the Flipkart security team.
Report Timeline:
Thu, 17 Dec 2020 - Reported to Security Team
18 Dec 2020 - First response from the team
28 Dec 2020 - Bug Accepted
5 Jan 2021 - Issue fixed
08 Jan 2021 - Acknowledged in their Hall of Fame.